In response to a growing trend in attacks that involve embedding malicious objects inside Office documents using the Object Packager control, Office made a change to the default activation model for Packager objects in Office applications.
Prior to this update, executables or scripts (e.g. EXE, JS, VBS) embedded using the Object Packager control can activate when a user double clicks on the embedded object within the document. For objects considered high risk by Windows, users will see a security warning as shown below.
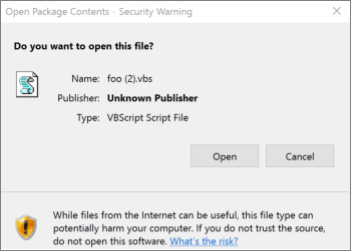
If the user clicks “Open”, the object executes with the privileges of the signed in user. Attackers abuse this vector to social engineer users to activate malicious programs embedded inside Office documents by persuading them to click through this warning prompt.
To protect users, Microsoft 365 applications will, by default, block activation of objects considered high risk. The list of extensions blocked will be the same one used by Outlook to block attachments. The list of extensions can be found in Blocked attachments in Outlook.
What does this behavior look like?
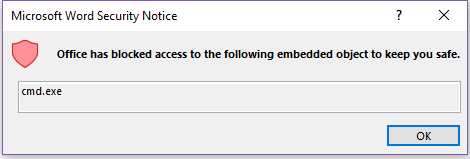
Office apps no longer allow the activation of objects that link to extensions that are considered high risk. When a user tries to activate such an object, they're shown the following notification:
Office has blocked access to the following embedded object to keep you safe.
Can I customize the extensions being blocked?
Yes, Office provides two Group Policy options that allow an administrator to customize which extensions are blocked. You'll find each of them under Office/Security Settings/.
Allow file extensions for OLE embedding
This policy setting allows you to specify which file extensions Office won’t block when they are embedded as an OLE package in an Office file by using the Object Packager control. If you enable this policy setting, enter the file extensions to allow, separated by semicolons.
For example: exe;vbs;js
Warning: Malicious scripts and executables can be embedded as an OLE package and can cause harm if clicked by the user. If extensions are added to this allow list, they can make Office less secure.
Block additional file extensions for OLE embedding
This policy setting allows you to specify additional file extensions that Office will block when they are embedded as an OLE package in an Office file by using the Object Packager control.
If you enable this policy setting, enter the additional file extensions to block, separated by semicolons.
For example: py;rb
Note: If you add a file extension under both “Allow file extensions for OLE embedding” and “Block file extensions for OLE embedding”, the extension will be blocked.
How do I change this behavior?
To change this behavior for a specific application such as Word or Excel you can create the following registry key: HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\<Office application>\Security\PackagerPrompt
Caution: Serious problems might occur if you modify the registry incorrectly by using Registry Editor or by using another method. These problems might require that you reinstall your operating system. Microsoft cannot guarantee that these problems can be solved. Modify the registry at your own risk.
To create the registry key:
-
Exit any Office applications that you might have open.
-
Start the Registry Editor by clicking Start (or pressing the Windows key on your keyboard) then typing Regedit and pressing enter.
-
Locate the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\<Office application>\Security\
Office application should be one of:
-
Word
-
Excel
-
PowerPoint
-
Visio
-
Publisher
-
-
Right click the key and add a new REG_DWORD hexadecimal value called PackagerPrompt with one of the following values:
-
0 – No prompt from Office when user clicks, object executes
-
1 – Prompt from Office when user clicks, object executes
-
2 – No prompt, Object does not execute
-
Have a question about Office that we didn't answer?
Visit the Microsoft Answers Community to see questions and answers posted by others or get answers to your own questions.










